Companies are leaning into IT outsourcing to tap into specialized skills and save on in-house costs. Surprisingly, more than cost-cutting drives these decisions. A well-structured IT outsourcing agreement can actually transform business technology, turning challenges like communication gaps and cultural barriers into advantages. This flips the script for any business leader who thought outsourcing was all risk and little reward.
Defining IT Outsourcing: Understanding the Basics
IT outsourcing represents a strategic business approach where organizations delegate their technology-related functions and processes to external specialized service providers. Understanding what is outsourced IT involves recognizing how companies can leverage external expertise to enhance technological capabilities without maintaining extensive internal infrastructure.
The Core Concept of IT Outsourcing
At its fundamental level, IT outsourcing involves transferring specific technological responsibilities to third-party providers who possess specialized skills and infrastructure. This practice allows businesses to focus on their core competencies while accessing advanced technological resources and expertise. The scope of IT outsourcing can range from specific technical support functions to comprehensive technology management strategies.
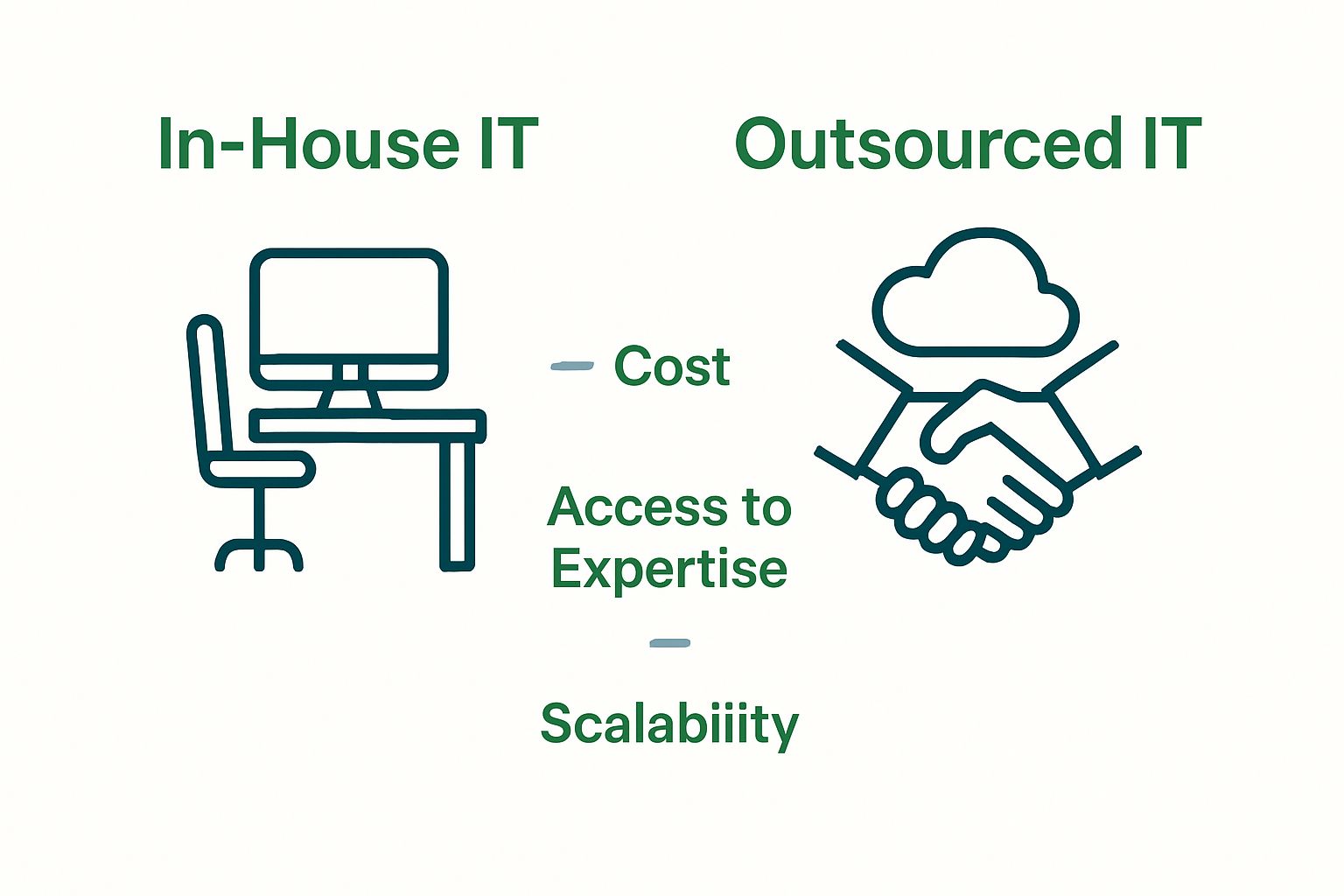
Key characteristics of IT outsourcing include:
- Accessing specialized technological skills without long-term employment commitments
- Reducing operational costs associated with maintaining extensive in-house IT departments
- Gaining flexibility in technological capabilities and scalability
Strategic Implications for Business Technology
Businesses leverage IT outsourcing not just as a cost-cutting measure but as a strategic tool for technological advancement. By partnering with external providers, organizations can tap into global talent pools, access cutting-edge technologies, and implement sophisticated technological solutions that might be challenging to develop internally.
Companies typically outsource various technological domains such as:
- Network infrastructure management
- Cybersecurity monitoring
- Web and software development
- Cloud computing services
- Email and collaboration platform support
The decision to outsource IT functions requires careful evaluation of organizational needs, potential risks, and expected technological outcomes.
To provide readers with a clear overview of the main types of challenges faced in IT outsourcing, the table below summarizes each challenge alongside its key impact on organizations.
| Challenge | Description | Potential Impact |
|---|---|---|
| Data Privacy and Protection | Safeguarding sensitive business and client information | Risk of data breaches, legal consequences |
| Communication Barriers | Difficulties in clear exchange between stakeholders | Misunderstandings, project delays |
| Service Quality Management | Ensuring delivered work meets required standards | Reduced performance, client dissatisfaction |
| Intellectual Property Risks | Protecting unique systems, software, and business data | Theft, loss of competitive advantage |
| Integration Complexities | Aligning outsourced solutions with existing systems | Increased cost, delayed implementation |
| Cost Overruns and Hidden Expenses | Unanticipated costs during or after project execution | Budget overruns, reduced ROI |
| Compliance and Regulatory Challenges | Adapting processes to meet legal and industry standards | Fines, operational disruptions |
The Importance of Addressing IT Outsourcing Challenges
Addressing IT outsourcing challenges is crucial for organizations seeking to maximize technological efficiency and maintain competitive advantage. Understanding why business owners outsource reveals that proactively managing potential obstacles can significantly impact the success of external technology partnerships.
Potential Risks and Strategic Management
IT outsourcing presents complex challenges that require strategic foresight and comprehensive planning. Organizations must recognize that while outsourcing offers numerous benefits, it simultaneously introduces potential vulnerabilities that demand careful navigation. **The primary risks include data security concerns, communication barriers, quality control issues, and potential misalignment of technological objectives.
**
Critical challenges businesses frequently encounter include:
- Maintaining data privacy and protection standards
- Ensuring consistent communication across geographic and cultural boundaries
- Managing performance expectations and service quality
- Protecting intellectual property rights
- Mitigating potential technological integration complexities
Strategic Framework for Challenge Resolution
Successful IT outsourcing requires a proactive and systematic approach to identifying, assessing, and mitigating potential challenges. Companies must develop robust frameworks that enable continuous monitoring, clear communication channels, and flexible adaptation strategies. This involves creating comprehensive service level agreements, establishing transparent performance metrics, and maintaining ongoing dialogue with external technology partners.
Key strategic considerations for effective challenge management include:
- Developing detailed contractual frameworks with clear expectations
- Implementing rigorous vendor selection processes
By recognizing and addressing potential challenges upfront, organizations can transform potential risks into opportunities for technological growth and innovation. Effective IT outsourcing is not about eliminating challenges completely, but about developing resilient, adaptive strategies that turn potential obstacles into competitive advantages.
Common Pitfalls in IT Outsourcing and Their Impact
IT outsourcing presents complex challenges that can significantly disrupt organizational technology strategies. Understanding IT outsourcing trends in 2025 helps businesses anticipate and mitigate potential risks inherent in external technological partnerships.
Communication and Alignment Challenges
One of the most critical pitfalls in IT outsourcing stems from communication breakdowns and misaligned expectations. Organizations frequently encounter significant obstacles when external technology providers fail to understand core business objectives or cannot effectively integrate with existing technological ecosystems. These communication gaps can lead to substantial inefficiencies, project delays, and increased operational complexity.
Key communication challenges include:
- Linguistic and cultural barriers between internal teams and external providers
- Inconsistent reporting and performance tracking mechanisms
- Misaligned technological expectations and implementation strategies
- Inadequate knowledge transfer protocols
- Unclear escalation and problem-resolution frameworks
Financial and Operational Risk Management
Financial risks represent another significant challenge in IT outsourcing. According to research examining technological outsourcing strategies, poorly structured outsourcing agreements can result in substantial hidden costs and unexpected expenditures. Businesses must develop comprehensive financial evaluation frameworks that extend beyond initial cost savings and consider long-term technological investment implications.
Critical financial and operational considerations include:
- Potential cost overruns due to poorly defined service agreements
- Unexpected infrastructure integration expenses
- Reduced operational flexibility
- Potential productivity losses during technological transitions
- Compliance and regulatory adaptation costs
Successful IT outsourcing demands a holistic approach that transcends traditional vendor-client relationships. Organizations must view external technology partnerships as collaborative ecosystems requiring continuous monitoring, transparent communication, and adaptive strategic frameworks.
Navigating Cultural and Communication Barriers
Cross-cultural communication represents a critical challenge in global IT outsourcing environments. Understanding and proactively addressing cultural nuances can dramatically improve collaboration and project success rates. Understanding IT outsourcing trends in 2025 highlights the increasing importance of developing sophisticated intercultural communication strategies.
Identifying Cultural Communication Challenges
IT outsourcing frequently involves collaboration across diverse geographic and cultural contexts, introducing complex communication dynamics. Research examining global technology collaboration reveals that cultural differences significantly impact technological project outcomes. These differences extend beyond language and manifest in communication styles, professional expectations, and workflow approaches.
Key cultural communication barriers include:
- Variations in hierarchical communication structures
- Different interpretations of professional feedback and criticism
- Contrasting approaches to time management and project deadlines
- Divergent decision-making processes
- Unique nonverbal communication signals and professional etiquette
Developing Effective Cross-Cultural Communication Strategies
Successful navigation of cultural barriers requires intentional, structured approaches that prioritize mutual understanding and respect. Organizations must invest in comprehensive cultural intelligence training, emphasizing adaptability, empathy, and proactive communication techniques.
Strategic approaches for mitigating cultural communication challenges involve:
- Implementing robust cross-cultural communication training programs
- Establishing clear, unambiguous communication protocols
- Creating multicultural teams with diverse perspectives
- Developing standardized documentation and communication templates
- Encouraging open dialogue about cultural differences
**Effective cross-cultural communication in IT outsourcing is not about eliminating differences, but creating collaborative frameworks that transform cultural diversity into a strategic advantage.
 **
**
Strategies for Mitigating IT Outsourcing Risks
Effective risk mitigation in IT outsourcing requires a comprehensive, proactive approach that addresses potential vulnerabilities across technological, operational, and strategic dimensions. Understanding why business owners outsource emphasizes the importance of developing robust protective frameworks.
Comprehensive Vendor Assessment Protocols
Selecting the right technology partner represents the foundational step in minimizing outsourcing risks. Organizations must implement rigorous vendor evaluation processes that extend beyond surface-level technical capabilities. This involves conducting thorough background checks, assessing technological infrastructure, reviewing past project performance, and validating cybersecurity standards.
Critical elements of comprehensive vendor assessment include:
- Detailed technological capability audits
- Financial stability and long-term sustainability analysis
- Comprehensive cybersecurity and data protection certifications
- Performance track record and client testimonial verification
- Alignment with industry-specific regulatory requirements
Contractual and Governance Framework Development
Developing precise, comprehensive contractual agreements forms a crucial risk mitigation strategy. According to research examining technological outsourcing strategies, well-structured contracts can significantly reduce potential operational uncertainties. Effective governance frameworks must include detailed service level agreements, clear performance metrics, and transparent accountability mechanisms.
Key contractual risk mitigation strategies involve:
- Establishing clear performance benchmarks and evaluation criteria
- Defining precise data security and confidentiality protocols
- Creating flexible contract modification provisions
- Implementing comprehensive exit strategy clauses
- Developing robust dispute resolution mechanisms
**Successful risk mitigation in IT outsourcing is not about eliminating all potential challenges, but creating adaptive, resilient frameworks that enable continuous improvement and strategic collaboration.
This table highlights proven strategies for proactively mitigating IT outsourcing risks, helping organizations better select partners and structure agreements for secure and successful partnerships.
| Risk Mitigation Strategy | Purpose | Key Actions |
|---|---|---|
| Comprehensive Vendor Assessment | Select reliable partners | Assess technical skills, financial health, cybersecurity |
| Detailed Contractual Frameworks | Set clear expectations and legal protections | Define SLAs, performance metrics, dispute process |
| Cybersecurity & Data Protection Protocols | Safeguard sensitive business information | Audit certifications, enforce strong security clauses |
| Performance Monitoring & Continuous Evaluation | Ensure ongoing quality and accountability | Regular reviews, benchmarks, reporting mechanisms |
| Cross-Cultural Communication Training | Improve team collaboration and reduce friction | Implement cultural awareness programs, clear protocols |
| Flexible Exit and Modification Clauses | Allow for adaptive change or project termination | Include exit strategies and adaptability terms |
Transform IT Outsourcing Challenges Into Opportunity with NineArchs LLC
Struggling with communication gaps, hidden costs, or complex vendor relationships in your IT outsourcing journey? If issues like misaligned expectations, cultural barriers, and data security risks are slowing your progress, you are not alone. The article highlights how these barriers can threaten your business agility and productivity. You need a partner that truly understands these pain points and can turn potential risks into real advantages.
Discover how NineArchs LLC makes IT outsourcing seamless, secure, and strategic. Our proven remote workforce solutions offer global expertise in custom software, virtual assistance, and BPO services, helping you overcome integration hurdles and compliance challenges with ease. Act now to shape a future where your technology evolves without limits. Visit NineArchs LLC to connect with experts who can help your business thrive today.
Frequently Asked Questions
What are the common challenges faced in IT outsourcing?
A: Common challenges in IT outsourcing include communication barriers, data security concerns, and misalignment of technological objectives. To address these, ensure you establish clear communication protocols and align project goals with your outsourcing partner.
How can I manage the risks associated with IT outsourcing?
A: To manage risks, conduct a thorough vendor assessment and develop comprehensive contractual agreements. Include performance metrics and clear accountability mechanisms in your contracts to protect your organization from potential issues.
What steps should I take to improve communication with my outsourcing partner?
A: Improve communication by implementing robust cross-cultural training programs and establishing unambiguous communication protocols. This can significantly enhance collaboration and project success rates.
How do I ensure data security when outsourcing IT functions?
A: Ensure data security by performing a cybersecurity audit of your vendor and outlining strict data protection protocols in your contract. Make it a priority to verify your partner’s cybersecurity certifications to mitigate risks effectively.
Why is cultural understanding important in IT outsourcing?
A: Cultural understanding is crucial because it can improve collaboration and help navigate diverse communication styles. Develop cross-cultural communication strategies that foster mutual respect and adaptability to enhance cooperation with your outsourced team.
What should I include in my service level agreement for IT outsourcing?
A: Include clear performance benchmarks, evaluation criteria, and data security protocols in your service level agreement. This specificity helps manage expectations and ensures accountability from your outsourcing partner.








[…] Learn more about navigating IT outsourcing challenges and develop a resilient strategy that balances operational efficiency with strategic risk management. […]
[…] Understanding IT Outsourcing Challenges Explained | NineArchs […]
[…] verification processes that validate the security capabilities of potential outsourcing partners. Understanding IT Outsourcing Challenges Explained provides deeper insights into navigating these complex security […]