Over eighty percent of american businesses report that data security is their number one concern when outsourcing IT services. With cyber threats evolving faster than ever, finding trustworthy technology partners can feel intimidating. This guide reveals the security essentials every american company needs to protect their information, explores real risks, and shows practical steps for building strong partnerships that keep sensitive data safe.
Role of Security in IT Outsourcing
Security represents a critical foundation in IT outsourcing, serving as the protective framework that safeguards organizational assets, sensitive information, and technological infrastructure. In an increasingly complex digital landscape, companies must strategically approach security when engaging external technology partners. The primary objective centers on maintaining comprehensive protection while leveraging external technological expertise.
Within IT outsourcing, security considerations span multiple critical domains. These include data protection protocols, access management systems, network defense strategies, compliance frameworks, and continuous risk monitoring. Organizations must implement rigorous verification processes that validate the security capabilities of potential outsourcing partners. Understanding IT Outsourcing Challenges Explained provides deeper insights into navigating these complex security dynamics.
Research consistently highlights three fundamental security dimensions in IT outsourcing. First, legal and contractual safeguards must explicitly define security expectations and accountability. Second, technological infrastructure requires robust encryption, multi-factor authentication, and advanced threat detection mechanisms. Third, ongoing security assessments and periodic vulnerability audits become essential to maintaining a proactive defense posture. Strategic management frameworks like ITIL recommend integrating comprehensive security measures that enhance operational efficiency while mitigating potential technological risks.
Practical security implementation involves several key strategies. Businesses should:
- Conduct thorough vendor security assessments
- Establish clear security performance metrics
- Define explicit data handling and protection protocols
- Implement continuous monitoring and reporting mechanisms
- Maintain transparent communication channels with outsourcing partners
By prioritizing security as a core component of IT outsourcing strategy, organizations can effectively balance technological innovation with risk management, creating resilient and adaptive technological ecosystems.
Key Security Risks and Threat Types
In IT outsourcing, understanding the complex landscape of cybersecurity threats is crucial for maintaining robust organizational defense mechanisms. The digital ecosystem presents numerous potential vulnerabilities that malicious actors continuously seek to exploit. These threats range from sophisticated technological breaches to subtle human-centered manipulation strategies, creating a multifaceted security challenge for businesses engaging external technology partners.
Cybersecurity research identifies several primary threat categories that organizations must vigilantly monitor. Malware attacks represent one of the most prevalent risks, including ransomware, trojans, and advanced persistent threats that can penetrate system infrastructures. Understanding What is Outsourced IT for Businesses offers comprehensive insights into managing these technological risks. Social engineering techniques pose another significant threat, where attackers manipulate human psychology to gain unauthorized system access. These methods often involve phishing emails, impersonation schemes, and psychological manipulation targeting employees with access to critical technological systems.
Supply chain attacks have emerged as a particularly insidious threat type in IT outsourcing environments. Cybercriminals strategically target less secure elements within interconnected technological ecosystems, using vulnerable third-party vendors as entry points to compromise larger organizational networks. These attacks exploit trust relationships and complex interdependencies between technology providers, making them exceptionally challenging to detect and mitigate. Key characteristics of supply chain threats include:
- Exploiting trusted vendor relationships
- Targeting smaller, less secure technological partners
- Implementing long-term, stealthy infiltration strategies
- Bypassing traditional perimeter security mechanisms
Practical defense strategies require a comprehensive, multilayered approach. Organizations must implement rigorous vendor security assessments, continuous monitoring protocols, and advanced threat detection technologies. By developing proactive security frameworks that anticipate and neutralize potential risks, businesses can create resilient technological infrastructures capable of withstanding increasingly sophisticated cyber threats.

Security Protocols and Compliance Standards
Compliance standards form the backbone of secure IT outsourcing, establishing critical guidelines that protect organizational data and technological resources. These comprehensive frameworks define the minimum security requirements organizations must implement when engaging external technology partners. The complexity of modern digital ecosystems demands sophisticated, adaptive security protocols that can respond to emerging technological challenges and potential vulnerabilities.
Role-Based Access Control (RBAC) emerges as a fundamental strategy in managing security protocols. Complete Guide to IT Support Outsourcing provides deeper context on implementing these critical access management techniques. This approach enables organizations to precisely define and restrict system access based on specific user roles, significantly reducing potential security risks. Key elements of robust RBAC implementation include:
- Granular permission settings
- Dynamic access management
- Continuous authentication mechanisms
- Comprehensive user activity logging
- Automated access revocation processes
International compliance standards play a pivotal role in establishing security benchmarks for IT outsourcing. Frameworks such as ISO 27001, GDPR, HIPAA, and PCI DSS provide structured guidelines for data protection, privacy, and security management. These standards require organizations to:
- Implement comprehensive risk assessment protocols
- Develop detailed incident response strategies
- Establish robust data encryption mechanisms
- Maintain transparent documentation of security practices
- Conduct regular security audits and vulnerability assessments
Effective security protocol implementation demands a holistic approach that combines technological solutions, legal frameworks, and organizational culture.
By integrating rigorous compliance standards with adaptive security technologies, businesses can create resilient outsourcing environments that protect sensitive information while maintaining operational flexibility and innovation potential.
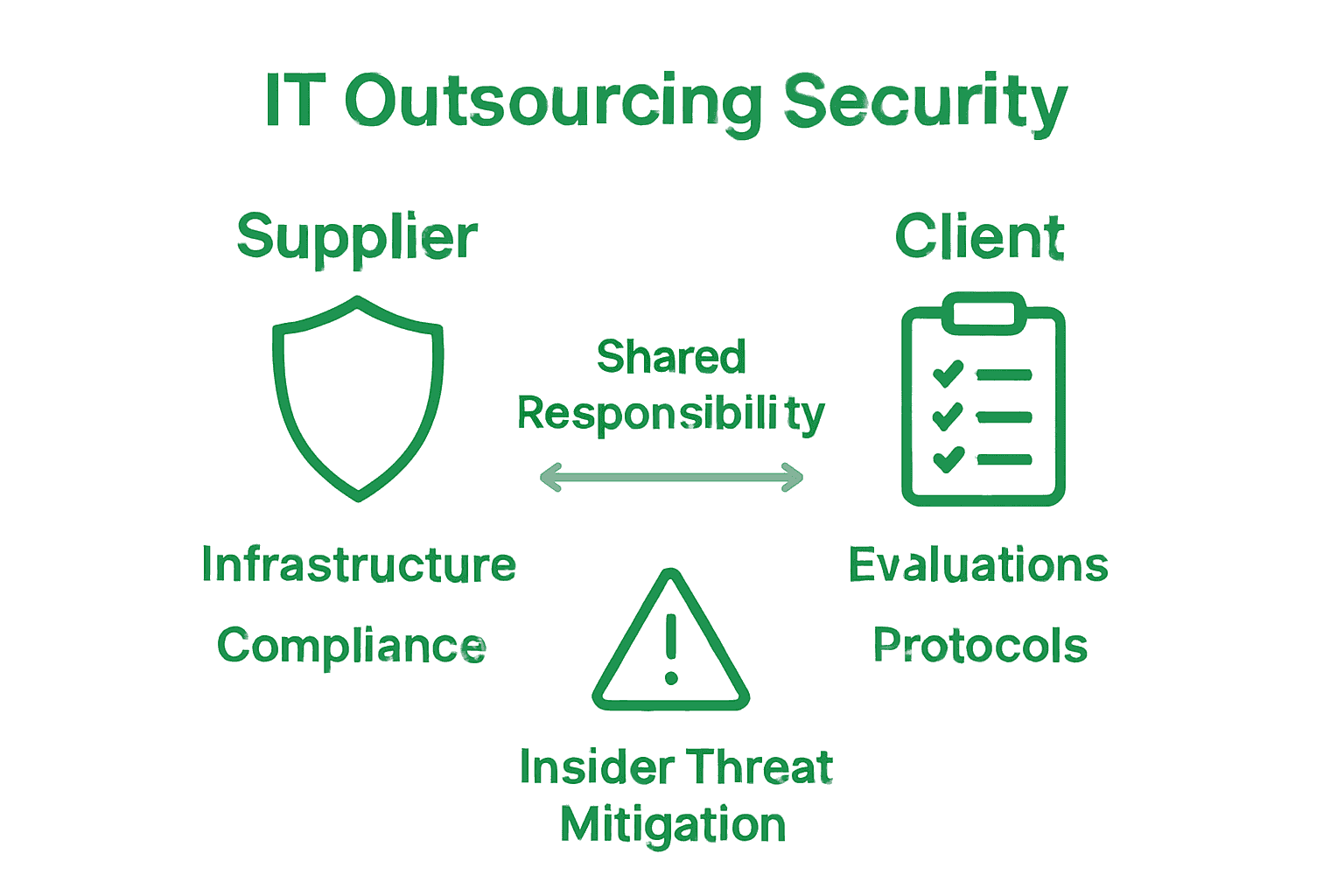
Supplier and Client Security Responsibilities
Security responsibilities in IT outsourcing represent a complex, collaborative ecosystem where both suppliers and clients must actively participate in maintaining comprehensive technological protection. This shared approach to security requires clear delineation of roles, expectations, and accountability mechanisms that prevent potential vulnerabilities and minimize risk exposure. Successful partnerships depend on transparent communication and mutual commitment to robust security practices.
Understanding IT Outsourcing Challenges Explained highlights the critical nature of defining explicit security responsibilities. Supplier responsibilities typically encompass:
- Implementing advanced security infrastructure
- Maintaining up-to-date technological defenses
- Providing comprehensive security training for personnel
- Developing incident response protocols
- Conducting regular internal security assessments
- Ensuring compliance with agreed-upon security standards
Client responsibilities are equally critical in maintaining a secure outsourcing environment. Organizations must actively engage in proactive security management by:
- Conducting thorough vendor security evaluations
- Establishing clear contractual security requirements
- Implementing continuous monitoring processes
- Defining explicit data handling and access protocols
- Maintaining robust internal security awareness programs
The concept of shared security responsibility extends beyond technical implementations to include insider threat mitigation. Both suppliers and clients must develop comprehensive strategies to address potential risks originating from human factors. This involves creating organizational cultures that prioritize security awareness, implementing strict access controls, and developing transparent communication channels that enable rapid identification and resolution of potential security incidents.
Mitigating Risks With Best Practices
Risk mitigation represents a strategic approach to managing potential vulnerabilities in IT outsourcing, requiring comprehensive and proactive security management. Organizations must develop sophisticated frameworks that anticipate, identify, and neutralize potential technological and operational risks before they can cause significant damage. This approach demands a holistic strategy that combines technological solutions, human expertise, and systematic risk assessment protocols.
Save Your Company from Suspicious Email with Proven Steps highlights critical strategies for identifying and preventing potential security breaches. Best practices for comprehensive risk mitigation include:
- Implementing multi-layered security architectures
- Developing robust incident response plans
- Conducting regular vulnerability assessments
- Maintaining comprehensive employee security training programs
- Establishing clear communication protocols
- Creating redundant backup and recovery systems
Effective risk mitigation demands a systematic approach to vendor selection and management. Organizations should:
- Perform thorough background checks on potential service providers
- Establish detailed security performance metrics
- Require transparent reporting of security incidents
- Develop comprehensive contractual security requirements
- Implement continuous monitoring and evaluation processes
The most successful risk mitigation strategies integrate technological solutions with human expertise. This requires creating a security-focused organizational culture that prioritizes proactive risk management, encourages ongoing learning, and maintains flexibility in responding to emerging technological challenges. By combining advanced security technologies with strategic human oversight, organizations can build resilient outsourcing environments that effectively protect sensitive information and technological assets.
Strengthen Your IT Outsourcing Security With Expert Solutions
Navigating the complex security landscape in IT outsourcing requires more than just awareness of risks like supply chain attacks and insider threats. The need to implement strong security protocols such as Role-Based Access Control and continuous vendor assessments is critical to protect your business assets and sustain operational growth. If you are seeking reliability and scalability while ensuring compliance with standards like ISO 27001 and GDPR, partnering with a trusted provider can turn these challenges into competitive advantages.
Elevate your security strategy by leveraging NineArchs LLC’s professional outsourcing and IT services. We specialize in tailored solutions that address your unique security concerns through rigorous vendor assessments, robust access management, and transparent communication channels. Don’t wait until vulnerabilities impact your business. Connect with our experts today to create a resilient IT outsourcing framework built on trust and innovation. Take the first step by visiting our contact page and learn more about how our custom software development and skills outsourcing services integrate seamlessly to keep your data safe. Explore how you can overcome typical IT outsourcing challenges by consulting with us now at Understanding IT Outsourcing Challenges Explained or deepen your insight into IT risk management at Understanding What is Outsourced IT for Businesses.
Frequently Asked Questions
What are the main security risks in IT outsourcing?
Security risks in IT outsourcing include malware attacks, social engineering techniques, and supply chain attacks. These threats can compromise organizational data and systems if not properly managed.
How can organizations ensure compliance with security standards in IT outsourcing?
Organizations can ensure compliance by implementing comprehensive risk assessment protocols, developing incident response strategies, maintaining robust data encryption, and conducting regular security audits and vulnerability assessments.
What responsibilities do suppliers and clients have regarding security in IT outsourcing?
Both suppliers and clients share security responsibilities. Suppliers must maintain advanced security infrastructure and conduct regular internal assessments, while clients need to engage in vendor evaluations and define clear data handling protocols.
What best practices should organizations follow for risk mitigation in IT outsourcing?
Best practices include implementing multi-layered security architectures, developing robust incident response plans, conducting regular vulnerability assessments, and maintaining comprehensive employee security training programs.
Recommended
- Complete Guide to IT Support Outsourcing | NineArchs
- Understanding IT Outsourcing Challenges Explained | NineArchs
- 7 Key Reasons to Outsource IT for Business Growth | NineArchs
- 7 Essential Outsourcing Best Practices for Success | NineArchs
- Complete Guide to Insurance Platform Security Fundamentals – Digital Insurance Platform | IBSuite Insurance Software | Modern Insurance System
- 7 conseils sécurité site internet pour PME et pros à succès – IT-Pascaud







